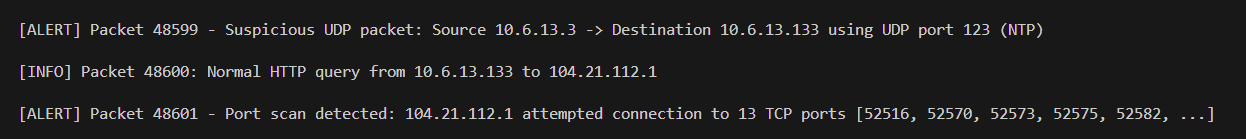
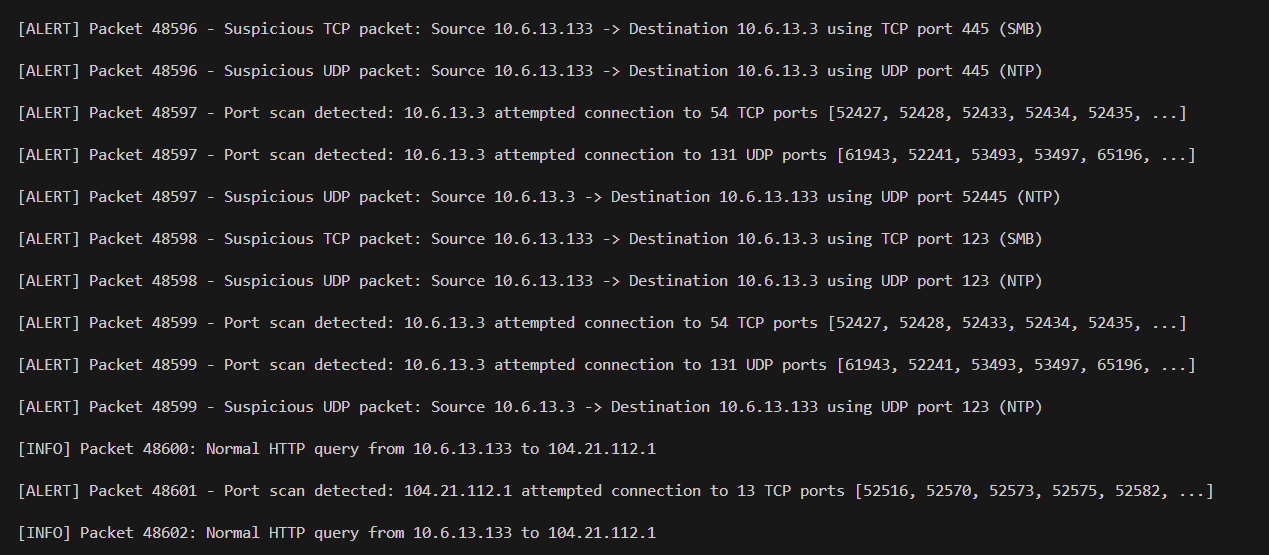
A Python NIDS that ingests .pcap files with Scapy, normalises packet metadata, and raises alerts for behaviours such as multi-port scans and traffic to risky services. Output is a skimmable alert stream using
[ALERT]/[INFO] lines that analysts can copy straight into tickets.
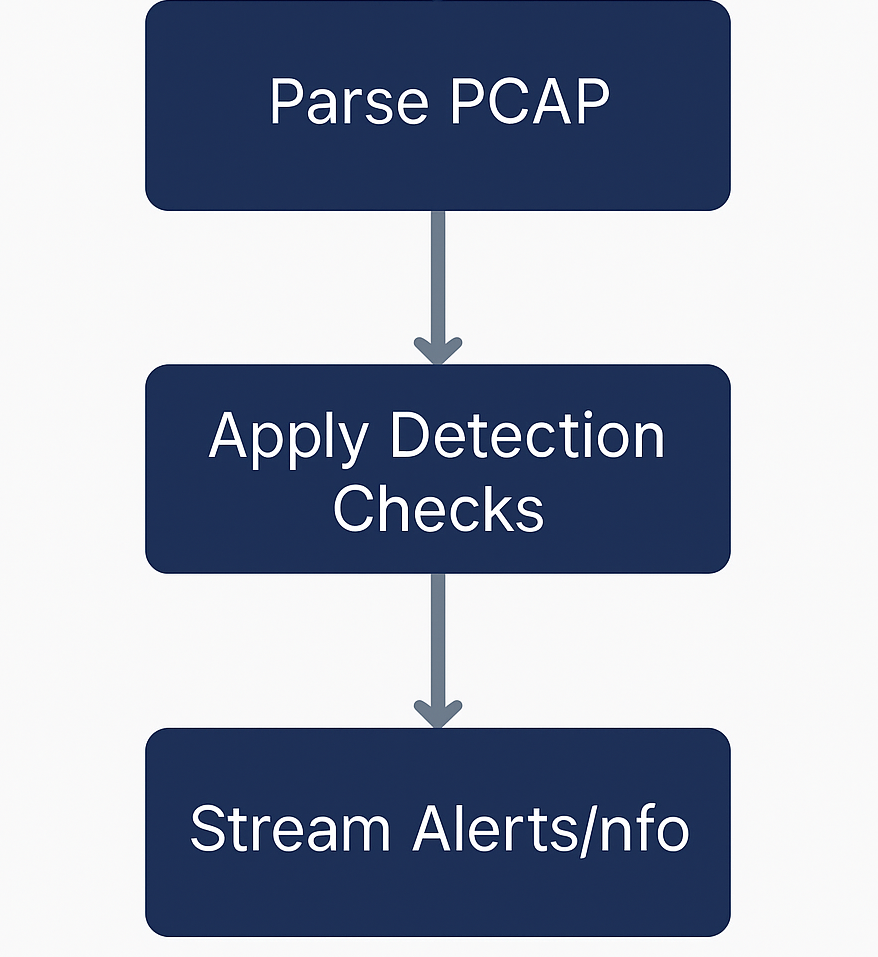
The brief: build a NIDS that ingests a PCAP, extracts key fields, applies at least two detection rules, and prints clear alerts for suspicious patterns. I implemented scan detection (unique-port fan-out) and risky-service detection (sensitive/abused ports).
rdpcap, layer access)src/dst, sport/dport, and TCP flags (if present). Normalise to a dict for easier counting.
(src,dst,proto) within a short window; flag when counts exceed a threshold (default ≥10). TCP focuses on SYNs to reduce noise.
{ ts, l3, l4, src, dst, sport, dport, tcp_flags }dport to the same dst (per protocol) in a short window.(src,dst) to prevent inflated counts.# From project root
python main.py
# Prompt:
# Please enter the pcap file to be scanned:
# (example) example.pcap
# The system parses the PCAP and streams [ALERT]/[INFO] lines.