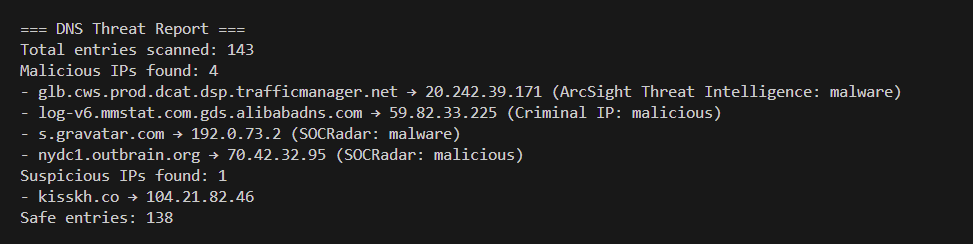
A lightweight Python tool that parses the local DNS cache (A/AAAA records), normalises entries, and enriches them with threat intelligence. The result is a concise DNS Threat Report that separates malicious, suspicious, and safe entries for fast SOC triage.
Why it matters: DNS is a rich telemetry source. Turning raw cache data into intel-backed findings helps identify beaconing, shady CDNs, and ad/malware infrastructure without deploying heavy agents.
ipconfig /displaydns output into structured indicators (FQDN ↔ IP).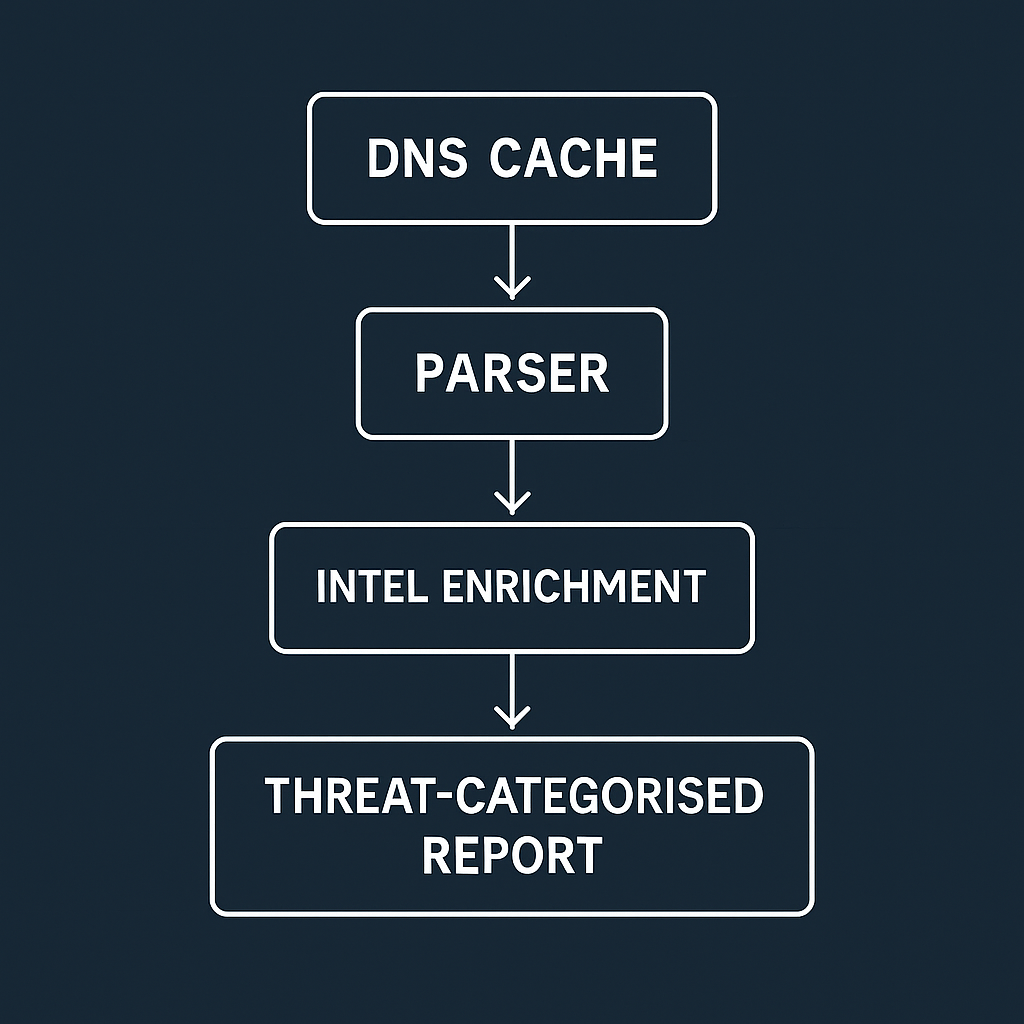
The goal was to practice end-to-end detection and enrichment: read the DNS cache, extract indicators, query reputation services, and produce an auditor-friendly report suitable for tickets or investigation notes.
ipconfig /displaydnsipconfig /displaydns and capture stdout.